We have done our best to curate and clarify The DAO hack developments. This page will be updated to reflect new developments. Do not hesitate to flag inconsistencies and suggest updates.
UPDATE 30 June: The envisioned temporary solution - a soft fork (see Q8 below), - has been discarded. The rationale is security: shortly after the technical implementation of the soft fork was proposed, a harmful attack vector was identified. This is a simple explanation of what it could cause to the network:
So, put simply: the soft-fork would allow an attacker to send many transactions to a mining node which the node would have to execute in order to detect that a call is being made to the contract. This would cost the attacker nothing and would slow down and potentially stop transaction mining while the soft fork is in place. A well-organised, well-financed attacker could probably cause substantial disruption to the network and reduce the fees you receive using this attack.
Although the vector was not used to attack the network so far, it bears the potential to significantly damage the network. Consequently, the soft fork as proposed a few days ago (see Q8. below) will not happen. The current options on the table are unclear, but discussions within the community start to show a growing acceptance of a hard fork (see Q10 below for what it is).
On 17 June 2016, an unknown individual or group exploited The DAO. The latter is the first and biggest crowdfunded and crowdequity-like fund based entirely on the Ethereum blockchain. If you would like to get an insight about The DAO, please read this explanation.
The attacker(s) exploited a software vulnerability and started draining ether from the primary address where it was stored. This attack resulted in the draining off of some 3.6 million ether from The DAO. This amounts to around a third of The DAO ether.
The drained ether was directed to what is referred to as a 'child DAO'. This 'child DAO' is an address where the sole curator is the attacker or group of attackers. Consequently, around a third of the total DAO fund got trapped in this 'child DAO'. Technicalities aside, the diverted assets cannot be withdrawn by the attacker for a total of 27 days following the creation of the child DAO.
In the following Q&A, we have done our best to untangle the complexities of the attack and explain their implications. As this is an evolving situation, we will certainly update our explainer to reflect new developments.
"Q1. So, you know who hacked The DAO?"
No, we do not. Outside of the perpetrator(s), nobody from the Ethereum community seems to know who the attacker(s) is(are). What is known at this time is that:
(a) the attacker(s) needed seven days to initiate the split;
(b) the two key contracts which held the tokens and allowed the recursive split were created two days before the attack; and
(c) the attacker(s) is(are) careful and used ether emanating from an account at ShapeShift.
"Q2. Was the hack, attack (as in a ‘bad action’)?"
The hack of The DAO is caused by a software vulnerability. Some might argue that the contract underlying The DAO allowed the exploit to happen and, therefore, the hack perpetrator ran a valid smart contract with a “draining feature”. There are, however, clear indications that the hack is ill-intentioned from its inception:
1/ The hacker considers the 3.6 million ether they drained from The DAO to be a reward for the exploit. This is contrary to The DAO’s mission, which is to fund projects.
2/ There is no way of independently validating that the “open letter” circulated a few days ago is indeed authored by the hack perpetrator. That text is the only public expression from the hacker or group of hackers, and its stance and tonality are clearly adversarial. The “open letter” contains no mention of a constructive approach, but includes an explicit formulation that the perpetrator rationally caused harm:
“I have carefully examined the code of The DAO and decided to participate after finding the feature where splitting is rewarded with additional ether.”
This sentence, as well as the whole letter, are a well-thought and calculated message. As aforementioned and clearly seen from this “open letter”, for the hacker, the end point of the operation was to keep the diverted funds, rather than fund companies.
3/ The perpetrator(s) offered to distribute funds (both bitcoin and ether) to miners who refuse to follow the proposed fork. Such a move is clearly aimed to damage trust and divide the Ethereum community, no matter whether said miners hold or not DAO tokens.
All things combined and all grains of salt added, it seems clear that the hacker's intent was to harm The DAO and the Ethereum community. The perpetrator’s ill-intentioned actions put a black mark of confidence against the field of crypto technologies. For those reasons, we qualify the hack as an attack, and the hack perpetrator(s) as attacker(s).
"Q3. OK, it sounds like some dude was nasty. The attack is made, ether has been diverted by a rogue actor. But then what do we do to fetch back the assets?"
That is the million-dollar question (no pun intended). Three main options exist; here, we do not go into the technical details, rather highlight the most significant outcomes of each option:
1/ Do nothing and leave it as is;
2/ Destroy the 'child DAO' to prevent the attacker(s) to get hold of the drained ether (also known as a soft fork; impacts the behaviour of the miners);
3/ Overwrite the Ethereum blockchain to erase the exploit and restore the situation as it were before the hack (also known as a hard fork).
Understandably, option #1 is the least desirable: the community, DAO token holders or not, is unwilling to leave the situation rot. Doing nothing would automatically result in several million ether seamlessly reach an unknown person or entity.
Option #2, the soft fork, is another way of dealing with the issue. Technicalities aside, such an operation is a one-time fix and would prevent the attacker(s) to withdraw the diverted ethers from the 'child DAO'. You may have guessed it: the soft fork would destroy the stolen ethers rather than return them to The DAO, and the thief would be gone. On 27 June, a soft fork implementation started being integrated (see Q6. below for details).
The 3rd option, referred to as the hard fork, is still highly contested. Indeed, this possibility would restore all the ether but would also alter the Ethereum blockchain significantly.
A quite obvious suggestion would be to drain back the child DAO to reset the ether where it originally belongs. As aforementioned, the attacker(s) being the sole curator, this is impossible. However, an alternative was proposed by Lefteris Karapetsas (CTO at Slock.it), involving a series of soft forks. This discussion explains the approach in greater detail.
Additional, alternative, options are on the table as well.
"Q4. OK, all that is a bit technical. I bought The DAO tokens - are those outside of the child DAO safe?"
Unfortunately not. The attacker(s) approach has the potential to drain all ether out of The DAO. The initial attack was interrupted after Ethereum’s co-founder, Vitalik Buterin, publicly outlined the possible fork options. Since the attacker(s) identity(ies) is(are) unknown, it is unclear what the rationale behind the interruption was.
There has been much activity on that side, so it is heavy to describe all of the details here. You may want to have a look at this overview for leads as it provides a synthetic scheme of the operations and identifies the accounts involved.
"Q5. I heard about a white hat attack against The DAO that was supposed to secure the drained ether. Was that successful?"
Yes and no. A group referred to as ‘Robin Hood’ indeed started off a white hat draining of The DAO. As the latter still contains ⅔ of the ether collected during the ‘fundraiser’, the rationale behind ‘Robin Hood’ was to secure the assets in a brand new, ‘white’ child DAO to prevent another major malevolent attack against the original DAO. The issue is that the attacker(s) has taken a stake in the rescue operation, enabling them to counter-attack the ‘Robin Hood’ led manoeuvre... Moreover, in this case, similarly to the initial rogue attack, the ether will not be available before a 27-day period expires.
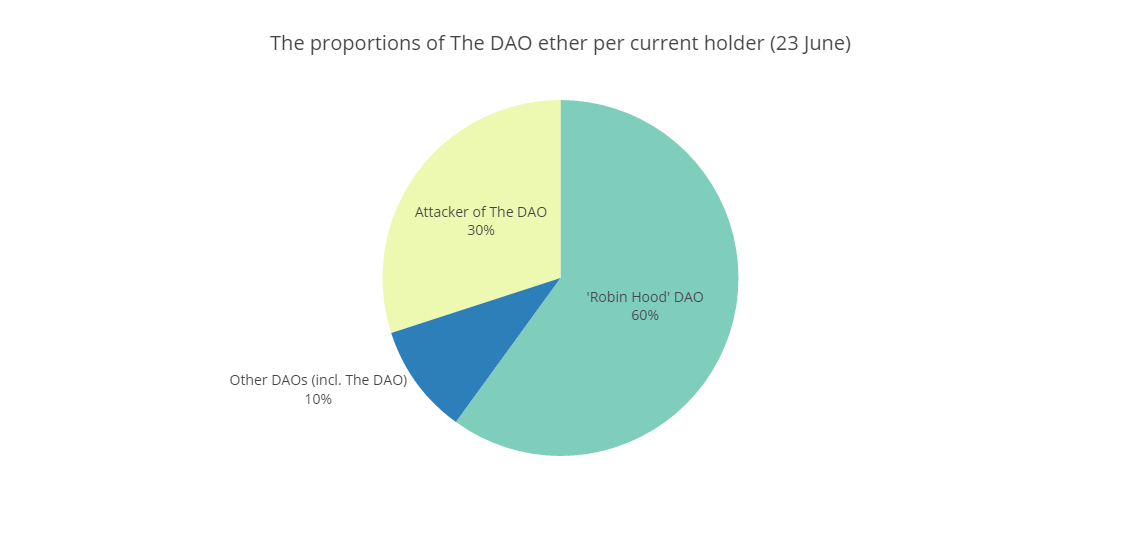
The proportions expressed above reflect the following ether amounts: The DAO has collected 12 million ether; 3.6 million of those are diverted and contained in the rogue child DAO. Another 7.2 million ether are currently secured in the ‘Robin Hood’ DAO. The remaining 1.2 million are allocated in both The DAO and other, smaller split DAOs.
"Q6. How are the exit options looking like at the moment? I gather this is a complicated question, but what could we envision as a way to contain the crisis?"
A positive note in this situation is that we have some time ahead of us. As aforementioned, the malicious child DAOs do not allow for ether to be withdrawn for 27 days after creation, which, at the time of writing, provides us with two and something weeks to elaborate a viable exit strategy.
A week after the attack, the following options were on the table:
1/ Do nothing: in this case, the ‘Robin Hood’ child DAO will release the ether it holds, the illegitimate splits would carry on with their ether. Additionally, the whole debacle would have serious repercussions on Ethereum as a community and as a network, and on ether as a cryptocurrency.
2/ A soft fork: It is important to highlight that the soft fork is a temporary solution that would insulate the ether from all DAOs from further interactions. Following the proposal in the wake of the malicious attack, such an operation would freeze all assets, regardless of which DAO they are in, and isolate them from anyone. This would freeze the total ether invested in The DAO ad vitam aeternam (which is significant as The DAO englobes nearly 16 percent of all ether on Earth).
3/ Another soft fork: it would limit all interactions with The DAO and the various child DAOs, except the ones whose curators are identified ‘white hats’. After a few months of cat-and-mouse, the ether from the ‘Robin Hood’-operated and the malevolent child DAOs would be fetched back and retributed to their initial investors. This operation could intervene as a follow-up of Option #2, thus preventing the ether to remain frozen forever.
4/ A hard fork: either without a prior soft fork or as a soft fork follow up. The outcome, as discussed in the wake of the malicious attack, would result in reverting the Ethereum blockchain back to a ‘sane’ block from before the attack, thus restoring all ether invested in The DAO to its initial owners with no monetary loss.
"Q7. So what is needed for the soft fork to happen?"
The activation requires a coordinated effort from 51 percent of the miners (to prevent the probability that miners from losing their ether). The coordination will outcome a block in the future which will be used to switch over to the new version of the blockchain.
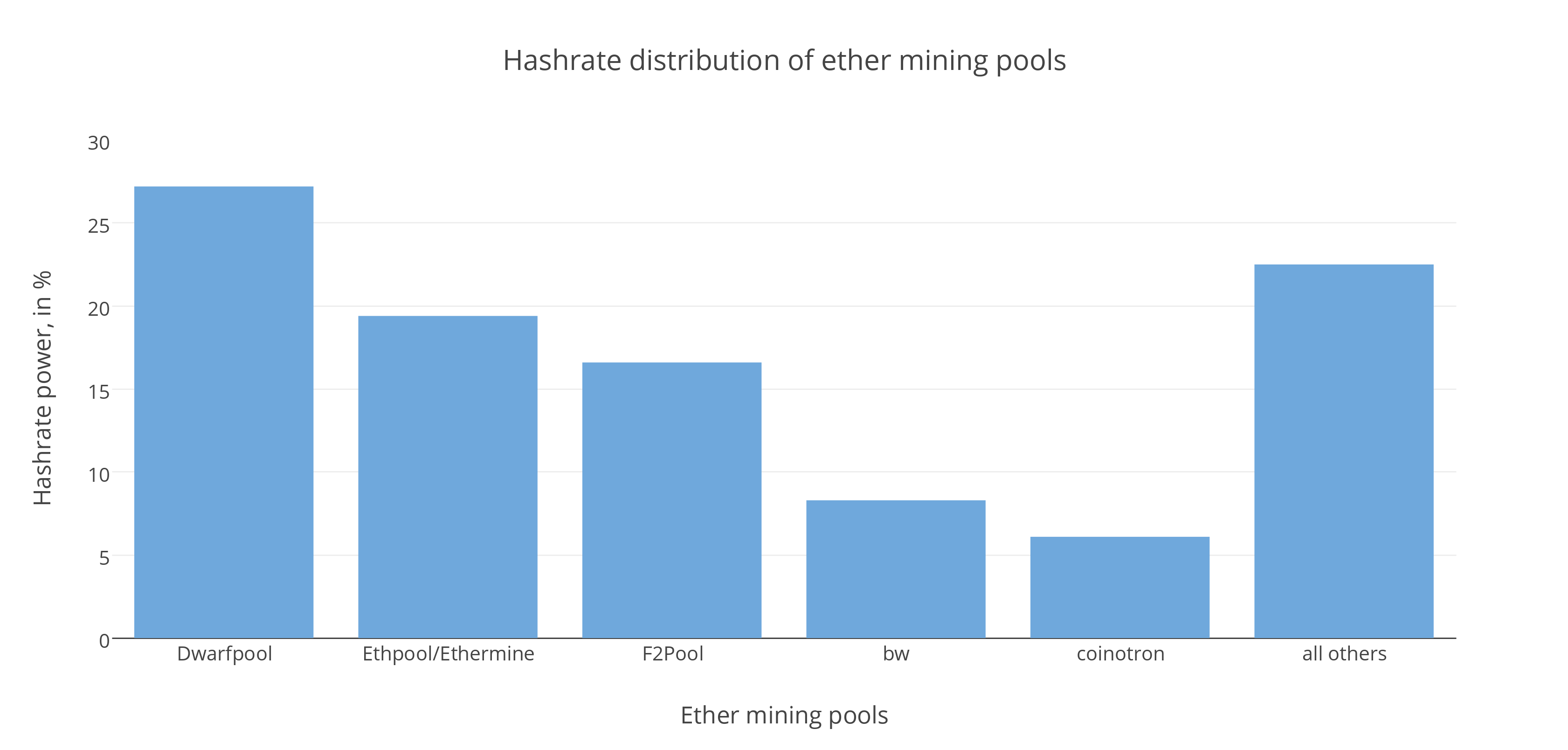
On 22 June, a voting on whether to implement a soft fork started on Ethpool and Ethermine. Dwarfpool, the largest ether mine, has already joined in although a little proportion of its hash power has taken a stance. The voting will end “a few days before the freeze period of the child DAO.”
"Q8. What did the vote on the soft fork say then?"
A large majority of miners have ‘voted’ in favour of a soft fork that has features from options #2 and #3 as described above (see Q6. above). In an update on the operation, the Ethereum Foundation said:
If the soft-fork passes, it will block all DAOs from releasing funds, not just the ones the community considers attacked. This is understandably undesired for all legitimately split DAOs. As such – if the community votes to enact the soft-fork – we propose a follow up patch to the soft-fork that will whitelist all DAOs split according to the intent upheld by the enacted soft-fork.
According to Etherchain.org, many mining pools have accepted the change underlying the proposed soft fork. Should that trend continue, the soft fork is expected to take hold on 30 June.
"Q9. So what if ever the soft fork failed?"
The outlook is messy. Vulnerability exploits are likely, by ‘black’ and ‘white’ hat hackers alike. Some mitigation tactics can be imagined to prevent significant amounts of tokens to be immediately diverted. However, that situation would be rather hopeless as it would amount to endless splitting, with potential ill-intentioned interventions (e.g., spamming the network, bribing miners to impact specific transactions, etc.). In this case, the perspective is gloom for The DAO tokens, which would lose any value. Preventing this apocalyptic scenario is a clear argument in favour of a soft fork.
"Q10. What about the hard fork - what is needed for it to happen?"
Since a hard fork would significantly impact the very structure of the Ethereum blockchain, activating that option will indeed require a well-elaborated consensus on how, what, when, etc. For a hard fork to occur, the key players of the Ethereum community (the Ethereum Foundation, the EthCore developers, etc.) are more important than the miners.
Naturally, all changes are possible, even creating new ether or destroying existing legit ether. It is unlikely that the community agrees with all the whimsical changes a hard fork bears the potential to introduce. A hard fork might be a way to retrieve all of The DAO tokens and create a different decentralised fund, focusing for ex. on bettering smart contracts security.
As of 29 June, the hard fork option is still hotly debated. We will update this content to reflect developments.
This article was originally written by Rayne Stamboliyska